Save Costs with Zscaler Remote Browser Access Instead of VDI
Discover how Zscaler Zero Trust solutions can significantly reduce costs and complexity compared to traditional VDI infrastructure and why we think VDIs are strategically dead.
The Hidden Costs of Traditional VDI Infrastructure
Traditional Virtual Desktop Infrastructure (VDI) setups come with a plethora of hidden costs that can strain your IT budget. From the need for hefty initial capital investments in servers and storage to ongoing operational expenditures, the financial burden is considerable. Additionally, maintaining a VDI environment demands specialized skills and constant management to ensure optimal performance and security.
Further complicating matters, VDIs often require costly Microsoft licenses for each virtual desktop, not to mention the overheads associated with regular software updates, patches, and troubleshooting. These factors collectively contribute to a significant operational expenditure (OPEX), making VDIs an expensive proposition for many organizations.
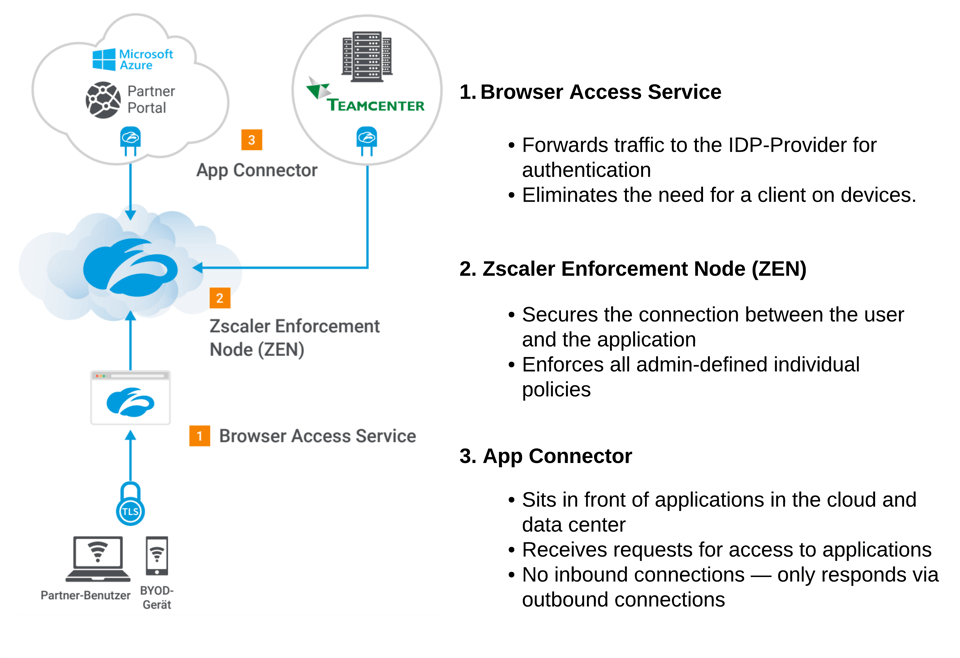
How Zscaler Remote Browser Access Eliminates the Need for VDI
Zscaler Remote Browser Access offers a modern solution that can effectively replace the need for traditional VDI setups. By leveraging cloud-based secure access, Zscaler Remote Browser Access allows users to connect to internal web applications seamlessly and securely through any web browser, eliminating the need for Windows-based virtual desktops.
This approach not only reduces the complexity associated with managing VDI environments but also significantly cuts down on costs. Without the need for extensive VDI infrastructure and Microsoft licenses, organizations can reallocate resources toward more strategic initiatives. The ease of use and minimal client requirements make Zscaler Remote Browser Access an efficient and cost-effective alternative.
- Bring Your Own Device (BYOD)
- External Support Access for OT Environments
- Privileged External Support for Server and Cloud Environments
- External Access for Partners
Enable BYOD and External Support Access Ultra Easy, Efficient & Secure
Zscaler allows external users to access any internal infrastructure regardless of its location (data center, cloud, branch) securely without the need of a internal device securely and easy by just using any browser. To securely expose a application it just takes a view clicks and minutes instead of concepts, deployments and hours or days. Agility is king. Companies with a shorter time to market gain advantage over those, who need weeks and months for such usecases.
Supported applications for this are:
- SSH
- RDP
- VNC
- HTTP(s)
This helps to get rid of your internal VDI infrastructure and enables the following usecases:
- Bring Your Own Device (BYOD)
- External Support Access for OT Environments
- Privileged External Support for Server and Cloud Environments
- External Access for Partners
Reducing Operational Complexity with Zscaler Privileged Remote Browser Access
Operational complexity can be a major hurdle in maintaining a robust IT environment. Zscaler Privileged Remote Access simplifies this by providing fast, direct, and secure access to critical systems and applications without the need for cumbersome VPNs or remote desktop clients.
With Zscaler's clientless access, remote workers and third-party vendors can securely connect to necessary resources from any browser. This eliminates the need for complicated network configurations and reduces the risk of security breaches associated with traditional remote access methods. The result is a streamlined, efficient operational setup that enhances productivity while minimizing potential vulnerabilities.
Security Features of Zscaler (Privileged) Remote Browser Access
Zscaler (Privileged) Remote Browser Access not only enhances user experience and simplifies infrastructure but also enforces strict access controls based on user identity and context rather than network location. This approach ensures that only authenticated and authorized users can access specific applications, significantly reducing the attack surface and preventing lateral movement within the network.
It also allows the sandbox inspection of uploaded files to hinder externals (accidentally) uploading infected files or malware. SSH-Keys and RDP-Credentials can be directly stored within the backend, so that that users do not need to handle this manually and more important: They do not see them, so they can not extract them.
Next to session recording for audit-purposes you can granular control what users can do within that sessions:
- Control Copy Paste from and to the window
- Control file up- and download from and to the application
Summary
VDIs are dead. 90% of the companies don`t need them anymore when using ZTNA. They lack of security, simplicity and deployment flexibility. Why should I deploy a VDI environment, when I can use the existing ZTNA Solution to securely expose any application to whom ever within 2 minutes? Of course I know: There might be databases, that are currently not supported. There might be legacy apps, that rely on a dozen of ports that do not go through https. Anyway: If you have that applications, then keep a minimal version of your VDI and think about redeploying them in a modern way to save costs and make your IT more agile.

