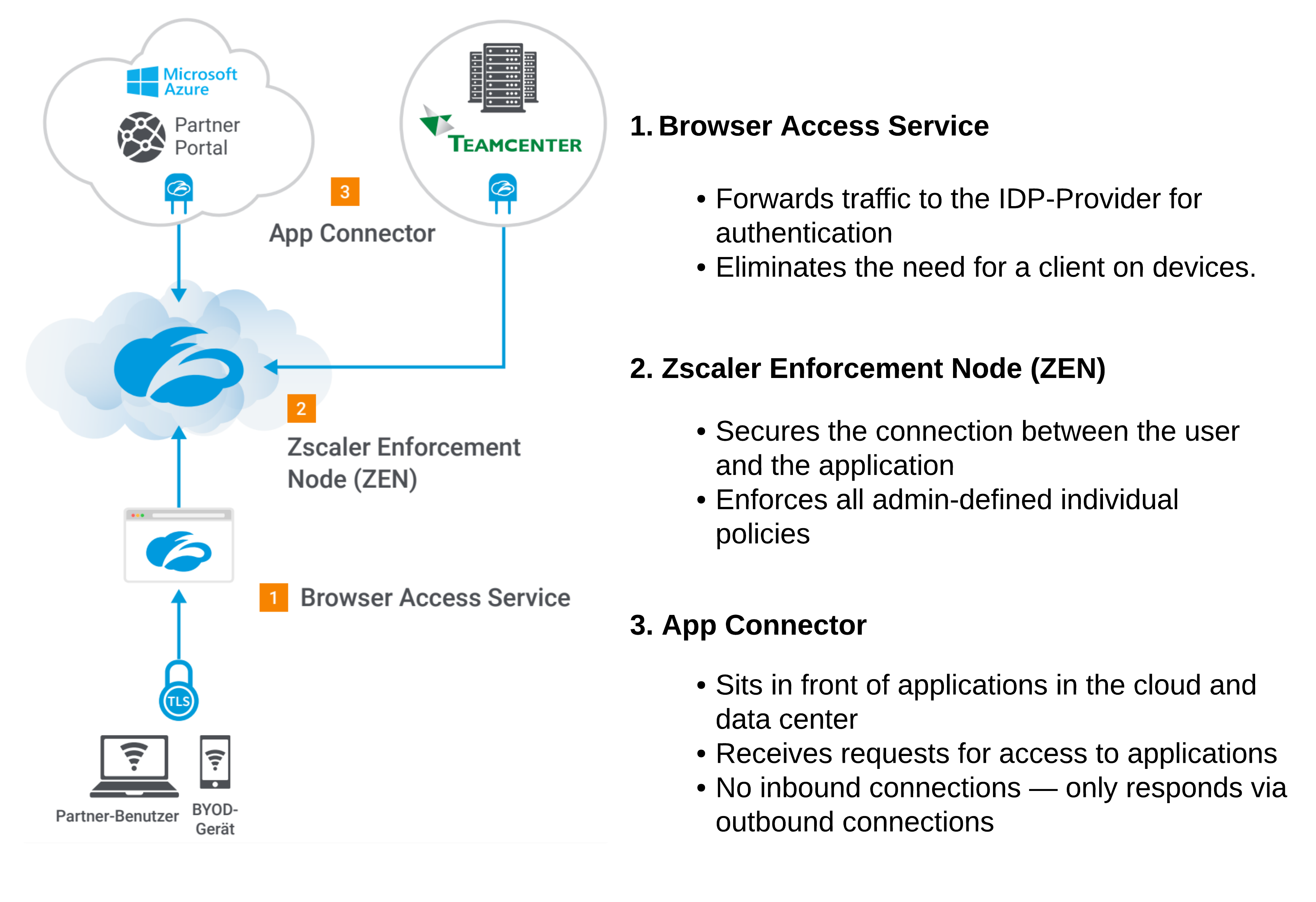
Zscaler Internet Access Service Status Monitoring With JumpCloud
This blog page focuses on Zscaler Internet Access(ZIA) service monitoring on the Client device and how to create alerting mechanism to inform Internal Security teams when the ZIA service disabled. The purpose behind this alerting to make sure to have visibility on the endpoint device and help to...